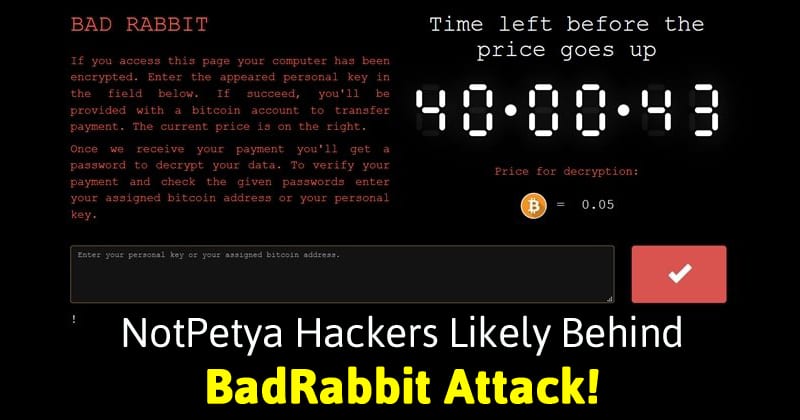
Well, Bad Rabbit malware is spreading as an infected Adobe Flash Player installer. Whenever users install the disguised Adobe Flash Player, all the files on the computer are immediately encrypted and the victims were asked to pay the ransom. According to the reports from Cisco Talos, Bad Rabbit ransomware seems to be based on DoublePulsar backdoor-based Nyetya malware that is based on Petya Ransomware. The same report also claims that the vast amount of Bad Rabbit’s code has also been rewritten. Well, earlier the reports from some popular source claim that NSA based exploits are not involved in this Bad Rabbit attack. However, Bad Rabbit uses an exploit which goes by the name EternalRomance to bypass security over SMB file-sharing connections. Hacker group Shadow brokers have published the EternalRomance exploit. However, Microsoft has patched the EternalRomance exploit way back in March 2016. Basically, the EternalRomance exploit overwrites the kernel’s session security context which enables the hacker to launch remote services. If that’s not enough for you, let me tell you that researchers have also found that the build toolchain for Bad Rabbit is very similar to Nyetya’s. Not only these, the techniques implemented in Bad Rabbit is also similar to Nyetya. For more details about Bad Rabbit, visit Cisco Talos blog post. So, what do you think about this? Share your views in the comment box below.
Δ